Understanding the Privacy Trap: How to Protect Your Business from Modern CIPA Lawsuits
Why standard tracking tags like Google Analytics, Meta Pixel, and LinkedIn Insight Tag are sparking lawsuits, and how simple compliance steps can save your company thousands.
Why This Matters — The Hidden Cost of Ignoring Privacy Laws
Over the past year, thousands of companies across the US have received privacy-violation notices under California law, even when they’re not based in California.
For example, one of my clients in New York, the case I was directly involved in, received a formal notice from a California law firm claiming that its website violated the California Invasion of Privacy Act (CIPA) because of a standard LinkedIn Insight Tag.
Here’s what unfolded:
A California consumer filed a privacy complaint handled by a specialist law firm.
Our client hired a defense attorney who charged $250 per hour and ended up charging a couple of thousand dollars.
His advice: “You can fight it, but litigation will take months and tens of thousands of dollars.”
The business ultimately settled for $18,000 to avoid the cost and distraction of a full lawsuit.
That’s the real problem: even when a company hasn’t done anything deliberately wrong, the cost, time, and uncertainty of litigation push many to settle quickly.
The simplest safeguard?
Install a reputable cookie-consent plugin (such as CookieYes, Cookiebot, or OneTrust) that blocks all marketing or analytics scripts until visitors give permission. This small step can make your website compliant and protect you from becoming a target.
What’s Going On?
Certain plaintiff law firms are now using older privacy statutes in new ways. They claim that modern tracking scripts, analytics tags, pixels, and SDKs act as “trap-and-trace devices” under California Penal Code § 638.51.
These laws were originally written to stop illegal telephone tapping. Today, they’re being stretched to cover online tracking that collects IP addresses or device information without explicit user consent.
So even standard tools such as Google Tag Manager, Google Analytics, Meta Pixel, or LinkedIn Tag can trigger lawsuits if they record identifying data before the visitor has opted in.
The Law in Plain English
CIPA § 638.51 prohibits anyone from “installing or using” a pen register or trap-and-trace device without a court order.
A “trap-and-trace” can now include software processes that record “routing or signaling” information, such as IP addresses or user-agent data.
Under § 637.2, plaintiffs can claim $5,000 per violation or three times actual damages, whichever is greater.
That “per violation” clause means every California visitor, or even every page load, can multiply exposure.
Why Routine Scripts Are Getting Flagged (and Court Trends)
Recent federal court decisions have encouraged this wave of litigation:
Greenley v. Kochava (S.D. Cal. 2023) – The court denied a motion to dismiss a claim that a mobile SDK capturing device and location data could be a “pen register.”
The judge held that CIPA’s definition covers both devices and processes that record signaling information, so software counts too.
Sources: Greenley v. Kochava decision (PDF) | K&L Gates analysis
Mirmalek v. Los Angeles Times Communications (2024) – The complaint alleged that third-party trackers on the LA Times website collected IP addresses and thus acted as trap-and-trace devices.
The case referenced Greenley as precedent, showing how quickly this theory spread.
Sources: ClassAction.org complaint PDF | Association of Corporate Counsel summary
Moody v. C2 Education Systems (C.D. Cal. 2024) – Involving a tutoring website that used a TikTok pixel.
The court again refused to dismiss, confirming that software-based tracking qualifies and that private individuals can sue under this section.
Sources: Paul Hastings analysis | WilmerHale 2024 Litigation Review
Even when companies act in good faith, courts are letting these cases proceed past early dismissal—forcing expensive settlements.
(K&L Gates overview: The Latest Wave of CIPA Litigation)
How to Check if Your Site Is at Risk
You don’t need to be technical—just follow these steps:
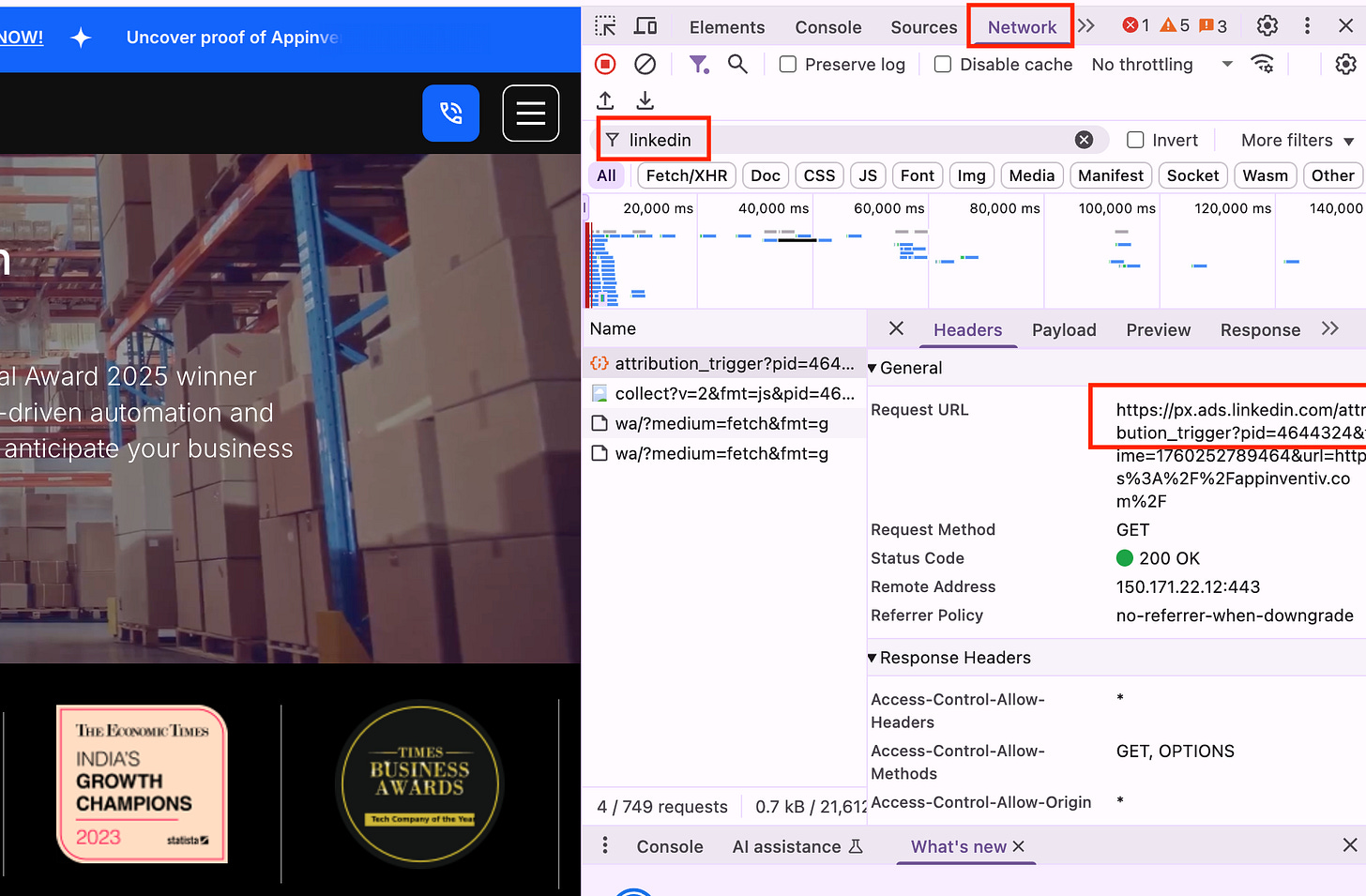
List all tags and pixels
Open a page → Right-click → Inspect → Network → Reload.
Look for calls to domains such as
linkedin.com,facebook.com, orgoogle-analytics.com.
Ask two simple questions
Do these scripts run before the visitor clicks “Accept”?
Do they capture IP addresses, device IDs, or browser fingerprints?
Test your consent banner
If any tracking starts automatically for visitors in California, you may be non-compliant.
Simple Fixes That Actually Work
Install a Cookie-Consent Plugin (quickest fix)
Tools such as **CookieYes,** Cookiebot, or OneTrust automatically block all non-essential scripts until the user agrees.
Configure them to show the banner on the first visit and especially to all US and EU visitors.
Use Server-Side Tagging
Route analytics data through your own server (e.g., Google Tag Manager Server-Side) and strip IP or user-agent details before forwarding.
Keep Records
Maintain:
A list of all active scripts and their purpose.
Proof that consent is logged before tags fire.
Screenshots of your banner settings and logic.
What It Means for Your Team
Marketing: Continue measuring performance, but gate everything behind consent.
Engineering: Default to privacy-by-design; anonymize IPs and deploy server-side tagging.
Legal/Compliance: Review all third-party scripts and maintain documentation showing consent and data-minimization practices.
The Bottom Line
California’s privacy laws now reach far beyond state borders. A single visit from a California user can expose any US business to CIPA trap-and-trace claims.
The good news is that compliance isn’t complicated:
Add a cookie-consent mechanism.
Control what data leaves your site.
Keep records proving consent.
These small steps can prevent costly legal headaches—and save your company tens of thousands of dollars in potential settlements and legal fees.